Port from Avnet's Internet Of Things full WiGo demo: SmartConfig - WebServer - Exosite - Android sensor Fusion App
Dependencies: NVIC_set_all_priorities mbed cc3000_hostdriver_mbedsocket TEMT6200 TSI Wi-Go_eCompass_Lib_V3 WiGo_BattCharger
Wi-Go Reference Design Overview
For additional information on Wi-Go, please visit http://www.em.avnet.com/wi-go
For additional information on Freescale eCompass, please visit
http://www.freescale.com/webapp/sps/site/prod_summary.jsp?code=E-Compass
Ported from Avnet's Wi-Go KEIL code.
Special thanks to Jim Carver from Avnet for providing the Wi-Go board and for his assistance.
Multiple Wi-Fi applications are provided within the latest version of Wi-Go software:
- SmartConfig App for auto-setup of Wi-Go network parameters.
- WebServer display of live sensor data.
- Exosite portal sensor data feed by Wi-Go.
- Freescale's Sensor Fusion App data feed by Wi-Go.
Wi-Go is intended for "untethered" portable operation (using it's high-capacity Lithium-Polymer battery). The serial terminal text interface is only required for initial setup, thereafter selection of an application from those available is via finger position on the Touch Slider during the initial 6 second startup period.
Running the Wi-Go Demo Suite
Warning
The on-board Firmware must be updated to mbed enable a Wi-Go system.
Goto the Component page to get the FirmwareUpdate tool (scroll down to the FirmwareUpdate topic).
MAG3110 sensor and eCompass Calibration!
As with the other sensor applications, the eCompass function requires quality calibration data to achieve best accuracy.
For the first 15 seconds after power-up it is recommended that "Figure 8" movements with Wi-Go be done in a smooth, repetitive pattern. Don't touch the slider pad during calibration.
Startup
The RGB LED blinks in a GREEN-ORANGE sequence to inform the user the module is waiting for input.
The RGB LED color designates which of the following Apps to launch.
| RGB LED Color | Application to Launch |
| Orange | Erase all wireless profiles |
| Purple | SmartConfig |
| Blue | WebServer |
| Red | Exosite Data Client |
| Green | Android Server |
Swipe your index finger across the slider pad, the RGB LED color will change at approximately 20% intervals.
Removing your finger latches the last color displayed. After about 3 seconds, the selected app will start.
Another app can be selected when the slider pad is touched again within the 3 seconds timeout.
After launch of Exosite or Android Server Apps, the eCompass function then controls the RGB LED.
(not in WebServer mode where RGB LEDs are manually controlled by the User).
| RGB LED Color | Direction Indication |
| Blue | Near to North |
| Green | North |
| Red | East / West |
| Purple | South |
__Note!__ The D1, D2 and D3 User LEDs on Wi-Go adhere to the following convention for the different Apps
| User LED# | Description of function controlling the LED |
| D1 | is the board heartbeat, derived from the timer interrupt |
| D2 | indicates network activity as follows: Web Server Wi-Go webpage is being served. Exosite Client Wi-Go is sending data. Android App Wi-Go is sending data |
| D3 | WLAN Network is Connected |
Detail of Wi-Go Applications
App #1: SmartConfig
See TI's pages on how to use the SmartConfig tool:
- Preferred method : Configuration using the SmartConfig tool
- SmartConfig download: Smart Config and Home Automation
- iOS app : available at Apple app store.
- Android app : download and install the Android SmartConfig Application on a PC.
This file contains the source code as well as the compiled APK file.
The APK file is stored inti\CC3000AndroidApp\SmartConfigCC3X\bin.
- iOS app : available at Apple app store.
App #2: WebServer display of live sensor data
__Note!__
When using the WebServer for the first time on a Wi-Fi network you will need to determine the IP address that's assigned to Wi-Go by the DHCP Server. To do this, it is recommended you use one of the following two methods:
- While Wi-Go is initially tethered to a laptop via USB, launch of the WebServer Application and note the IP address that is reported on the terminal screen immediately after selection of this App.
- Alternatively, use a 3rd party LAN SCAN type tool to view Wi-Go's IP address.
eg.FING, - available for free download from Google Play or iTunes App Stores…
Wi-Go's WebServer Application is selected as follows:
- Press RESET, followed by the
eCompass Calibration(mentioned at the top of this page).
Then use index finger on slider to select the WebServer App (RGB LED = BLUE).
At end of the 3 second selection period the WebServer App shall launch.
- If you are tethered to a laptop and have a terminal open the Wi-Fi network connection confirmation will be seen, eg.
'*** Wi-Go board DHCP assigned IP Address = 192.168.43.102
- Once you have noted Wi-Go's reported IP address, the USB cable may be disconnected and Wi-Go then used as intended, running on it's own battery power.
- Use an Internet Browser on SmartPhone/Tablet/Laptop (connected to same Hot-Spot/Wireless Router subnet), to now connect to the noted Wi-Go IP address and view the WebServer output:
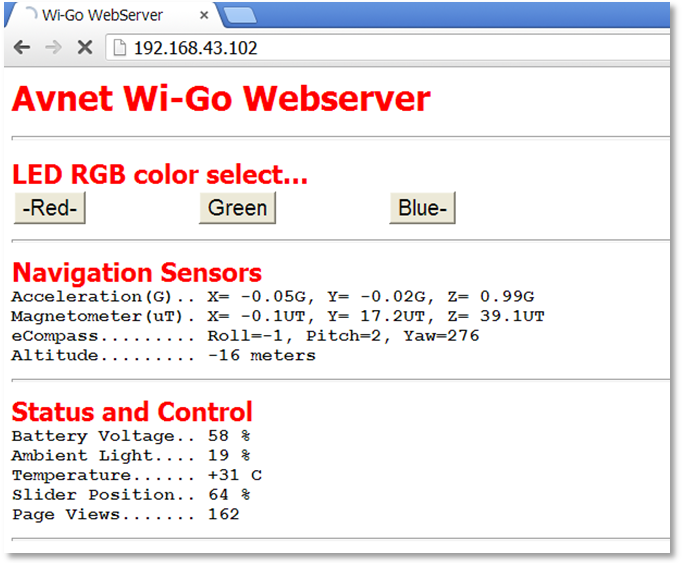
- the Webserver sensor data is auto-updated every 2 seconds a manual refresh (F5 on laptop).
- In the event of an error, press refresh to regenerate the screen.
- Use the mouse (or touch-screen) to exercise the RGB LED output.
App #3: Exosite Data Client
Wi-Go's sensor data gets transmitted via Wi-Fi to a cloud-based Exosite portal where the sensor measurements are displayed graphically on a "dashboard". Users can create unique customized dashboards using drag and drop GUI widgets from the library provided on the Exosite website.
__Note!__ For the Exosite application a "live" connection to the Internet is required !!!
- Press RESET, followed by the
eCompass Calibration(mentioned at the top of this page).
Then use index finger on slider to select the Exosite Client App (RGB LED = RED) - On launching this App, note Wi-Go's MAC address displayed on your terminal
(if not running a terminal use FING or other WLAN Scan tool to determine Wi-Go's MAC address)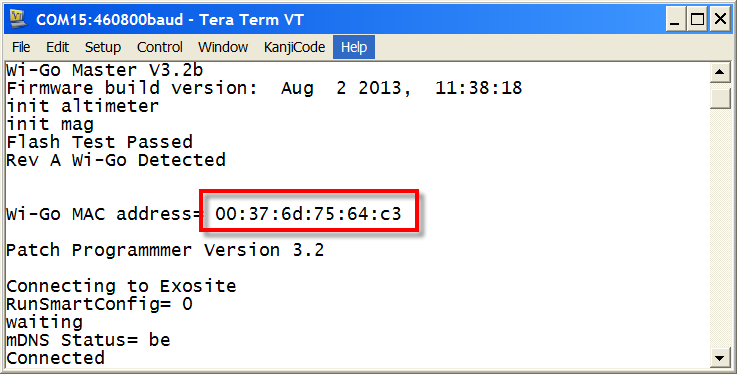
- Using your computer's internet browser, go to avnet.exosite.com and sign-up for a free
Avnet TrialExosite Account: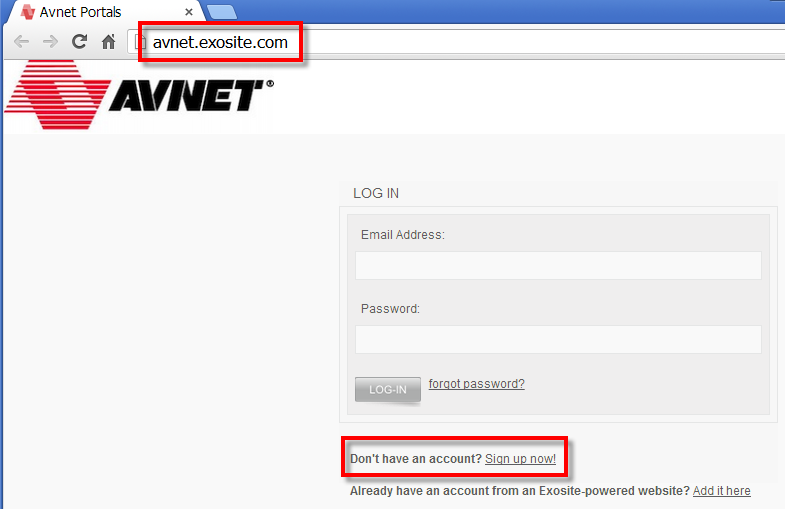
- On the next screen, click on the Sign-Up Now button in the displayed
Avnet Trialaccount option. - Complete the Account Info and Contact Info then click on Create Account (make sure to use a valid email address!).
- Check for new incoming email from avnet.exosite.com to the address you provided and click on the link in this email to activate your new Exosite account.
- Once activated, login using the email address and password that you chose in your registration.
Your Exosite Portal and Dashboard should now display. The first time you log-in to your new account, the default Home dashboard will be displayed, pre-configured with two widgets. On the left is the Welcome widget for tips and information. On the right is the Device List widget.
Dashboards are configurable, so at any time this default dashboard can be changed, widgets deleted and added (Clicking the upside-down triangle icon in a widget's Title bar will allow you to edit it). - Before going further with the Dashboard, you need to connect your Wi-Go device to your Exosite account. Do this by going to the left sidebar and selecting Devices followed by selecting the +Add Device link (on right of screen).
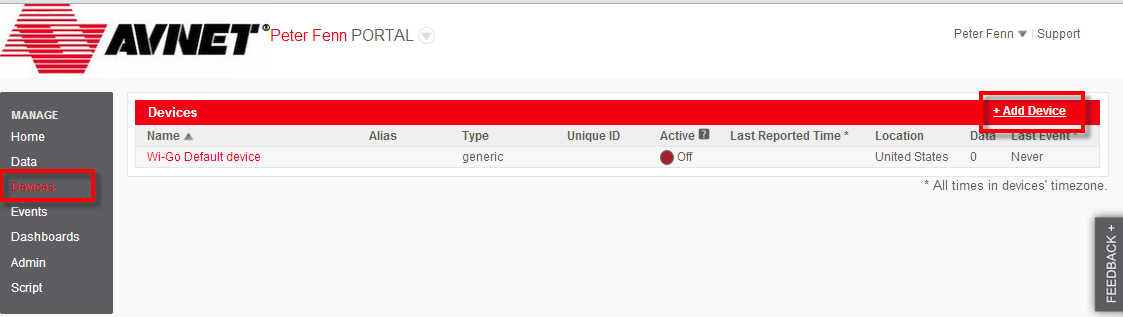
- In the Setup screens that follow, enter the following
| Select a supported device | Wi-Go |
| Enter device MAC Address | nn:nn:nn:nn:nn:nn [your Wi-Go's MAC address including colons] |
| Enter device Name | [choose a descriptive name] |
| Enter device Location | [description of your location] |
- Once completed, under Devices the name chosen for the added Wi-Go device should now be listed.
- Click on this new Wi-Go device to examine (and edit if necessary) it's Device Information screen.
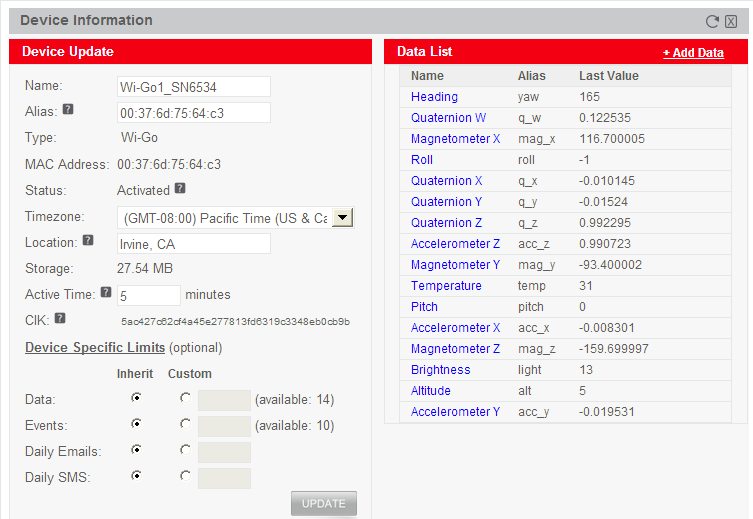
- Click the CLOSE button to exit the Device Information screen.
- On your Wi-Go kit now press RESET, followed by the
eCompass Calibration(mentioned at the top of this page)
and again select the Exosite Client App (RGB LED = RED) using your index finger. - Refresh your browser (press F5) a couple've times until the Active indicator changes to On (Green).
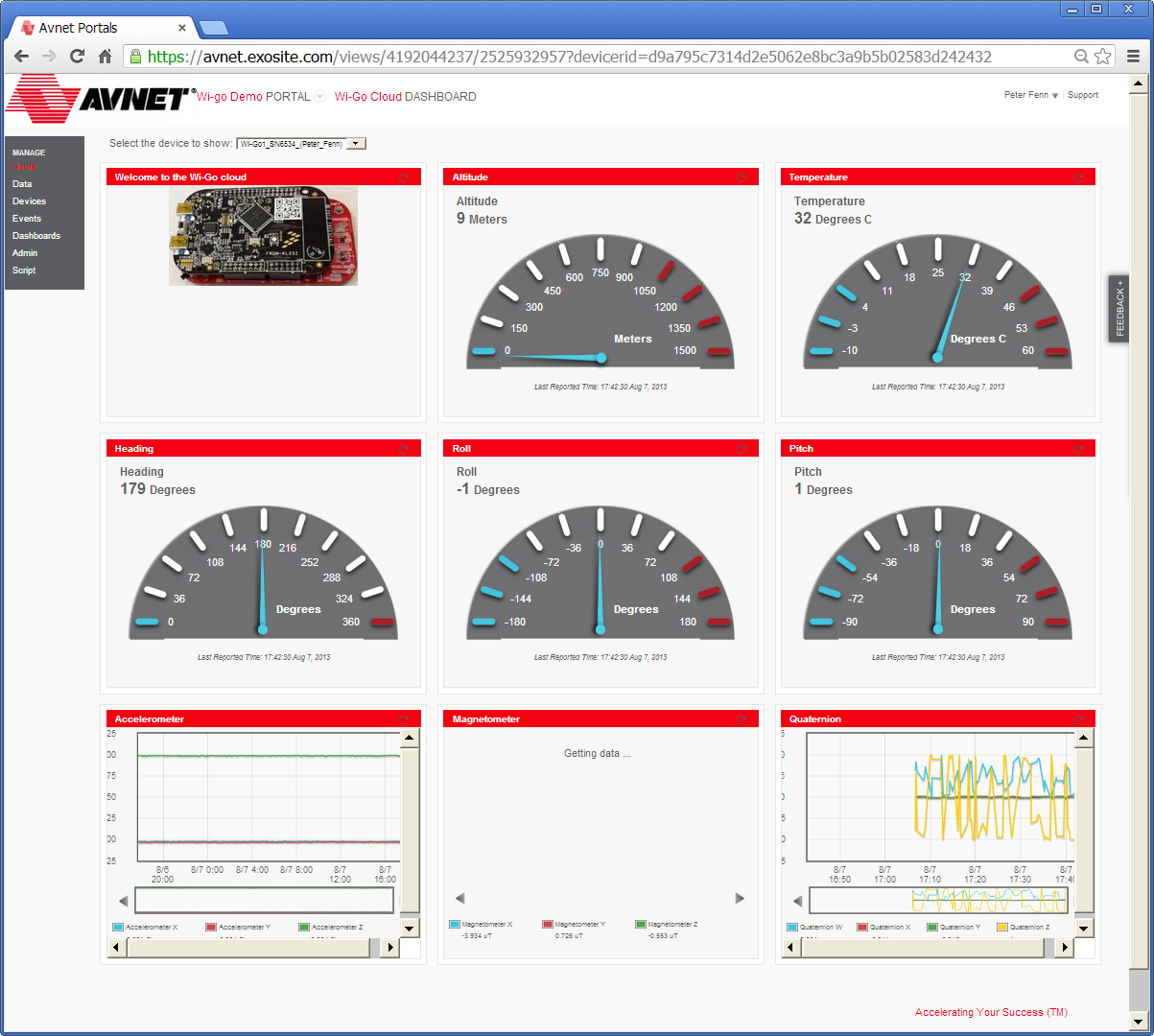
- From the left sidebar click on Home and click on the recently named Wi-Go device which is located under the Device List.
This will bring-up a default dashboard display similar to what's shown below.
(Dashboards are typically accessed via the Dashboards menu entry). Check the dashboard is updating with live data by moving your Wi-Go Kit through different orientations.
- To create a custom dashboard, select Dashboards from the sidebar menu, followed by +Add Dashboard (on right side of Your Dashboards title bar). After completion of the initial configuration screen you will then be able to add Widgets to display the various Wi-Go data sources as well as pictures and text to support your application.
- More guidance on the creation, editing and sharing of custom dashboards is available under the Exosite support pages
App #4: Android Sensor Fusion App
- Press RESET, followed by the
eCompass Calibration(mentioned at the top of this page)
, then use index finger on slider to select the Android App (RGB LED = GREEN)
- Freescale's ''Xtrinsic Sensor Fusion Toolbox'" will run on Android 3.0 or above phone or tablet. Free to download from Google Play, type Sensor fusion in the search box to find it.
freescale.sensors.sfusion

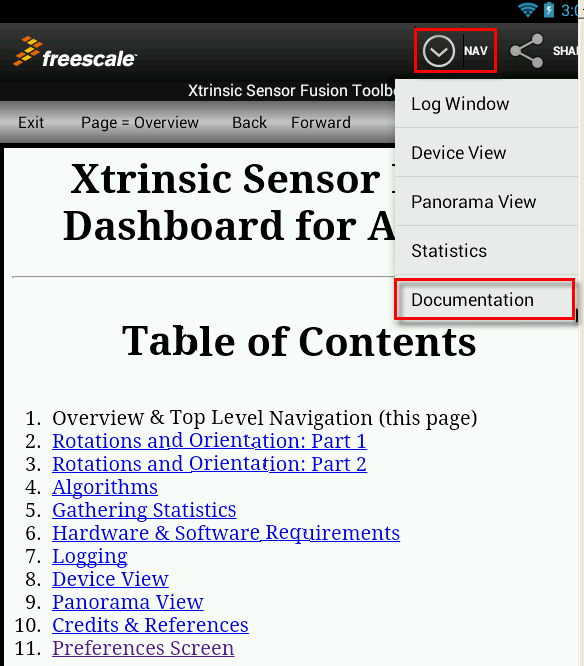
- The Freescale App is well documented. To access the built-in documentation, press the NAV button at top of screen followed by Documentation from the scroll-down menu:
- Freescale's sensors site provides additional resources such as this overview:
free-android-app-teaches-sensor-fusion-basics
- Go to the Options Menu and select Preferences…
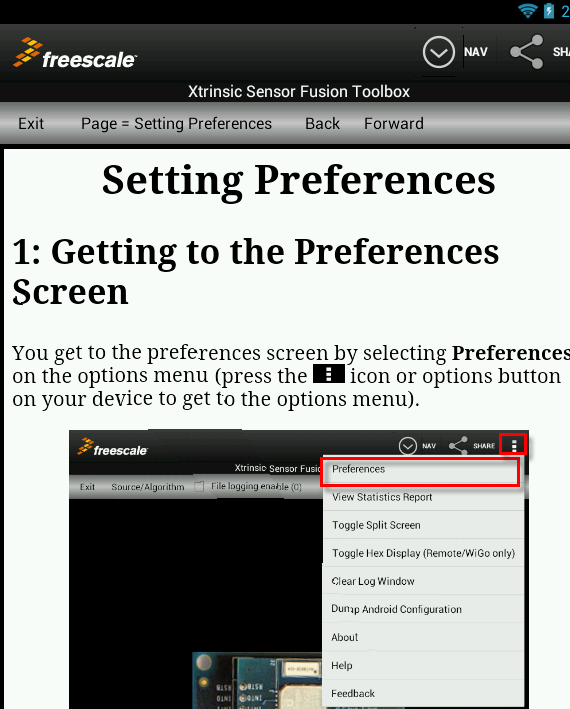
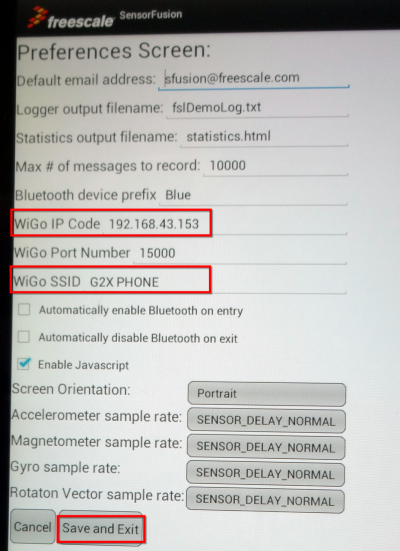
- The following items need to be taken care of:
| Enter WiGo's IP address |
| Enter the SSID (of the Hot-Spot or Wireless Access Point used by Wi-Go) |
- Press Save and Exit!
- Exit the Application completely then re-launch the Sensor Fusion Application.
- Select the ''Source/Algorithm'" menu and change the data source to Wi-Go mag/accel
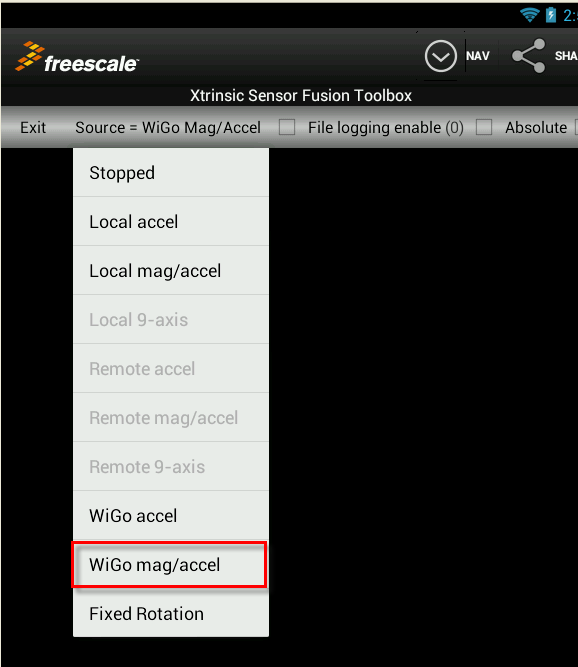
- The Android App should now be displaying a 3-D image of Wi-Go that you can rotate and flip-over by moving the Wi-Go board accordingly…
- Use NAV > Device View to display if this view does not come-up by default.

- A Serial Terminal connection is not necessary but if you happen to have one open you should see the following messages as Wi-Go connects to the Android App:
"Server waiting for connection" followed by
"connected, transmit buffer size= 96", and then
"input = 0123456789"
at which time Wi-Go starts streaming data to the Android App.
cc3000_hostdriver_mbedsocket/cc3000_wlan.cpp@1:99bfc8d68fd3, 2013-10-23 (annotated)
- Committer:
- frankvnk
- Date:
- Wed Oct 23 12:01:30 2013 +0000
- Revision:
- 1:99bfc8d68fd3
Webserver functional using ProcessWlanInterrupt flag instead of NVIC
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| frankvnk | 1:99bfc8d68fd3 | 1 | /***************************************************************************** |
| frankvnk | 1:99bfc8d68fd3 | 2 | * |
| frankvnk | 1:99bfc8d68fd3 | 3 | * C++ interface/implementation created by Martin Kojtal (0xc0170). Thanks to |
| frankvnk | 1:99bfc8d68fd3 | 4 | * Jim Carver and Frank Vannieuwkerke for their inital cc3000 mbed port and |
| frankvnk | 1:99bfc8d68fd3 | 5 | * provided help. |
| frankvnk | 1:99bfc8d68fd3 | 6 | * |
| frankvnk | 1:99bfc8d68fd3 | 7 | * This version of "host driver" uses CC3000 Host Driver Implementation. Thus |
| frankvnk | 1:99bfc8d68fd3 | 8 | * read the following copyright: |
| frankvnk | 1:99bfc8d68fd3 | 9 | * |
| frankvnk | 1:99bfc8d68fd3 | 10 | * Copyright (C) 2011 Texas Instruments Incorporated - http://www.ti.com/ |
| frankvnk | 1:99bfc8d68fd3 | 11 | * |
| frankvnk | 1:99bfc8d68fd3 | 12 | * Redistribution and use in source and binary forms, with or without |
| frankvnk | 1:99bfc8d68fd3 | 13 | * modification, are permitted provided that the following conditions |
| frankvnk | 1:99bfc8d68fd3 | 14 | * are met: |
| frankvnk | 1:99bfc8d68fd3 | 15 | * |
| frankvnk | 1:99bfc8d68fd3 | 16 | * Redistributions of source code must retain the above copyright |
| frankvnk | 1:99bfc8d68fd3 | 17 | * notice, this list of conditions and the following disclaimer. |
| frankvnk | 1:99bfc8d68fd3 | 18 | * |
| frankvnk | 1:99bfc8d68fd3 | 19 | * Redistributions in binary form must reproduce the above copyright |
| frankvnk | 1:99bfc8d68fd3 | 20 | * notice, this list of conditions and the following disclaimer in the |
| frankvnk | 1:99bfc8d68fd3 | 21 | * documentation and/or other materials provided with the |
| frankvnk | 1:99bfc8d68fd3 | 22 | * distribution. |
| frankvnk | 1:99bfc8d68fd3 | 23 | * |
| frankvnk | 1:99bfc8d68fd3 | 24 | * Neither the name of Texas Instruments Incorporated nor the names of |
| frankvnk | 1:99bfc8d68fd3 | 25 | * its contributors may be used to endorse or promote products derived |
| frankvnk | 1:99bfc8d68fd3 | 26 | * from this software without specific prior written permission. |
| frankvnk | 1:99bfc8d68fd3 | 27 | * |
| frankvnk | 1:99bfc8d68fd3 | 28 | * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS |
| frankvnk | 1:99bfc8d68fd3 | 29 | * "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT |
| frankvnk | 1:99bfc8d68fd3 | 30 | * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR |
| frankvnk | 1:99bfc8d68fd3 | 31 | * A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT |
| frankvnk | 1:99bfc8d68fd3 | 32 | * OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, |
| frankvnk | 1:99bfc8d68fd3 | 33 | * SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT |
| frankvnk | 1:99bfc8d68fd3 | 34 | * LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, |
| frankvnk | 1:99bfc8d68fd3 | 35 | * DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY |
| frankvnk | 1:99bfc8d68fd3 | 36 | * THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT |
| frankvnk | 1:99bfc8d68fd3 | 37 | * (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE |
| frankvnk | 1:99bfc8d68fd3 | 38 | * OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. |
| frankvnk | 1:99bfc8d68fd3 | 39 | * |
| frankvnk | 1:99bfc8d68fd3 | 40 | *****************************************************************************/ |
| frankvnk | 1:99bfc8d68fd3 | 41 | #include "cc3000.h" |
| frankvnk | 1:99bfc8d68fd3 | 42 | |
| frankvnk | 1:99bfc8d68fd3 | 43 | namespace mbed_cc3000 { |
| frankvnk | 1:99bfc8d68fd3 | 44 | |
| frankvnk | 1:99bfc8d68fd3 | 45 | cc3000_wlan::cc3000_wlan(cc3000_simple_link &simple_link, cc3000_event &event, cc3000_spi &spi, cc3000_hci &hci) : |
| frankvnk | 1:99bfc8d68fd3 | 46 | _simple_link(simple_link), _event(event), _spi(spi), _hci(hci) { |
| frankvnk | 1:99bfc8d68fd3 | 47 | |
| frankvnk | 1:99bfc8d68fd3 | 48 | } |
| frankvnk | 1:99bfc8d68fd3 | 49 | |
| frankvnk | 1:99bfc8d68fd3 | 50 | cc3000_wlan::~cc3000_wlan() { |
| frankvnk | 1:99bfc8d68fd3 | 51 | |
| frankvnk | 1:99bfc8d68fd3 | 52 | } |
| frankvnk | 1:99bfc8d68fd3 | 53 | |
| frankvnk | 1:99bfc8d68fd3 | 54 | void cc3000_wlan::simpleLink_init_start(uint16_t patches_available_host) { |
| frankvnk | 1:99bfc8d68fd3 | 55 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 56 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 57 | |
| frankvnk | 1:99bfc8d68fd3 | 58 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 59 | args = (uint8_t *)(ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 60 | |
| frankvnk | 1:99bfc8d68fd3 | 61 | UINT8_TO_STREAM(args, ((patches_available_host) ? SL_PATCHES_REQUEST_FORCE_HOST : SL_PATCHES_REQUEST_DEFAULT)); |
| frankvnk | 1:99bfc8d68fd3 | 62 | |
| frankvnk | 1:99bfc8d68fd3 | 63 | // IRQ Line asserted - send HCI_CMND_SIMPLE_LINK_START to CC3000 |
| frankvnk | 1:99bfc8d68fd3 | 64 | _hci.command_send(HCI_CMND_SIMPLE_LINK_START, ptr, WLAN_SL_INIT_START_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 65 | _event.simplelink_wait_event(HCI_CMND_SIMPLE_LINK_START, 0); |
| frankvnk | 1:99bfc8d68fd3 | 66 | } |
| frankvnk | 1:99bfc8d68fd3 | 67 | |
| frankvnk | 1:99bfc8d68fd3 | 68 | void cc3000_wlan::start(uint16_t patches_available_host) { |
| frankvnk | 1:99bfc8d68fd3 | 69 | uint32_t spi_irq_state; |
| frankvnk | 1:99bfc8d68fd3 | 70 | |
| frankvnk | 1:99bfc8d68fd3 | 71 | _simple_link.set_sent_packets(0); |
| frankvnk | 1:99bfc8d68fd3 | 72 | _simple_link.set_number_of_released_packets(0); |
| frankvnk | 1:99bfc8d68fd3 | 73 | _simple_link.set_op_code(0); |
| frankvnk | 1:99bfc8d68fd3 | 74 | _simple_link.set_number_free_buffers(0); |
| frankvnk | 1:99bfc8d68fd3 | 75 | _simple_link.set_buffer_length(0); |
| frankvnk | 1:99bfc8d68fd3 | 76 | _simple_link.set_buffer_size(0); |
| frankvnk | 1:99bfc8d68fd3 | 77 | _simple_link.set_pending_data(0); |
| frankvnk | 1:99bfc8d68fd3 | 78 | _simple_link.set_transmit_error(0); |
| frankvnk | 1:99bfc8d68fd3 | 79 | _simple_link.set_data_received_flag(0); |
| frankvnk | 1:99bfc8d68fd3 | 80 | _simple_link.set_buffer_size(0); |
| frankvnk | 1:99bfc8d68fd3 | 81 | |
| frankvnk | 1:99bfc8d68fd3 | 82 | // init spi |
| frankvnk | 1:99bfc8d68fd3 | 83 | _spi.open(); |
| frankvnk | 1:99bfc8d68fd3 | 84 | // Check the IRQ line |
| frankvnk | 1:99bfc8d68fd3 | 85 | spi_irq_state = _spi.wlan_irq_read(); |
| frankvnk | 1:99bfc8d68fd3 | 86 | // ASIC 1273 chip enable: toggle WLAN EN line |
| frankvnk | 1:99bfc8d68fd3 | 87 | _spi.set_wlan_en(WLAN_ENABLE); |
| frankvnk | 1:99bfc8d68fd3 | 88 | |
| frankvnk | 1:99bfc8d68fd3 | 89 | if (spi_irq_state) |
| frankvnk | 1:99bfc8d68fd3 | 90 | { |
| frankvnk | 1:99bfc8d68fd3 | 91 | // wait till the IRQ line goes low |
| frankvnk | 1:99bfc8d68fd3 | 92 | while(_spi.wlan_irq_read() != 0) |
| frankvnk | 1:99bfc8d68fd3 | 93 | { |
| frankvnk | 1:99bfc8d68fd3 | 94 | } |
| frankvnk | 1:99bfc8d68fd3 | 95 | } |
| frankvnk | 1:99bfc8d68fd3 | 96 | else |
| frankvnk | 1:99bfc8d68fd3 | 97 | { |
| frankvnk | 1:99bfc8d68fd3 | 98 | // wait till the IRQ line goes high and then low |
| frankvnk | 1:99bfc8d68fd3 | 99 | while(_spi.wlan_irq_read() == 0) |
| frankvnk | 1:99bfc8d68fd3 | 100 | { |
| frankvnk | 1:99bfc8d68fd3 | 101 | } |
| frankvnk | 1:99bfc8d68fd3 | 102 | while(_spi.wlan_irq_read() != 0) |
| frankvnk | 1:99bfc8d68fd3 | 103 | { |
| frankvnk | 1:99bfc8d68fd3 | 104 | } |
| frankvnk | 1:99bfc8d68fd3 | 105 | } |
| frankvnk | 1:99bfc8d68fd3 | 106 | simpleLink_init_start(patches_available_host); |
| frankvnk | 1:99bfc8d68fd3 | 107 | |
| frankvnk | 1:99bfc8d68fd3 | 108 | // Read Buffer's size and finish |
| frankvnk | 1:99bfc8d68fd3 | 109 | _hci.command_send(HCI_CMND_READ_BUFFER_SIZE, _simple_link.get_transmit_buffer(), 0); |
| frankvnk | 1:99bfc8d68fd3 | 110 | _event.simplelink_wait_event(HCI_CMND_READ_BUFFER_SIZE, 0); |
| frankvnk | 1:99bfc8d68fd3 | 111 | } |
| frankvnk | 1:99bfc8d68fd3 | 112 | |
| frankvnk | 1:99bfc8d68fd3 | 113 | |
| frankvnk | 1:99bfc8d68fd3 | 114 | void cc3000_wlan::stop() { |
| frankvnk | 1:99bfc8d68fd3 | 115 | // ASIC 1273 chip disable |
| frankvnk | 1:99bfc8d68fd3 | 116 | _spi.set_wlan_en( WLAN_DISABLE ); |
| frankvnk | 1:99bfc8d68fd3 | 117 | |
| frankvnk | 1:99bfc8d68fd3 | 118 | // Wait till IRQ line goes high... |
| frankvnk | 1:99bfc8d68fd3 | 119 | while(_spi.wlan_irq_read() == 0) |
| frankvnk | 1:99bfc8d68fd3 | 120 | { |
| frankvnk | 1:99bfc8d68fd3 | 121 | } |
| frankvnk | 1:99bfc8d68fd3 | 122 | |
| frankvnk | 1:99bfc8d68fd3 | 123 | _spi.close(); |
| frankvnk | 1:99bfc8d68fd3 | 124 | } |
| frankvnk | 1:99bfc8d68fd3 | 125 | |
| frankvnk | 1:99bfc8d68fd3 | 126 | |
| frankvnk | 1:99bfc8d68fd3 | 127 | int32_t cc3000_wlan::disconnect() { |
| frankvnk | 1:99bfc8d68fd3 | 128 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 129 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 130 | |
| frankvnk | 1:99bfc8d68fd3 | 131 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 132 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 133 | |
| frankvnk | 1:99bfc8d68fd3 | 134 | _hci.command_send(HCI_CMND_WLAN_DISCONNECT, ptr, 0); |
| frankvnk | 1:99bfc8d68fd3 | 135 | |
| frankvnk | 1:99bfc8d68fd3 | 136 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 137 | _event.simplelink_wait_event(HCI_CMND_WLAN_DISCONNECT, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 138 | errno = ret; |
| frankvnk | 1:99bfc8d68fd3 | 139 | |
| frankvnk | 1:99bfc8d68fd3 | 140 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 141 | } |
| frankvnk | 1:99bfc8d68fd3 | 142 | |
| frankvnk | 1:99bfc8d68fd3 | 143 | |
| frankvnk | 1:99bfc8d68fd3 | 144 | int32_t cc3000_wlan::ioctl_set_connection_policy(uint32_t should_connect_to_open_ap, |
| frankvnk | 1:99bfc8d68fd3 | 145 | uint32_t use_fast_connect, |
| frankvnk | 1:99bfc8d68fd3 | 146 | uint32_t use_profiles) { |
| frankvnk | 1:99bfc8d68fd3 | 147 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 148 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 149 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 150 | |
| frankvnk | 1:99bfc8d68fd3 | 151 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 152 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 153 | args = (uint8_t *)(ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 154 | |
| frankvnk | 1:99bfc8d68fd3 | 155 | // Fill in HCI packet structure |
| frankvnk | 1:99bfc8d68fd3 | 156 | args = UINT32_TO_STREAM(args, should_connect_to_open_ap); |
| frankvnk | 1:99bfc8d68fd3 | 157 | args = UINT32_TO_STREAM(args, use_fast_connect); |
| frankvnk | 1:99bfc8d68fd3 | 158 | args = UINT32_TO_STREAM(args, use_profiles); |
| frankvnk | 1:99bfc8d68fd3 | 159 | |
| frankvnk | 1:99bfc8d68fd3 | 160 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 161 | _hci.command_send(HCI_CMND_WLAN_IOCTL_SET_CONNECTION_POLICY, ptr, WLAN_SET_CONNECTION_POLICY_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 162 | |
| frankvnk | 1:99bfc8d68fd3 | 163 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 164 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_SET_CONNECTION_POLICY, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 165 | |
| frankvnk | 1:99bfc8d68fd3 | 166 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 167 | } |
| frankvnk | 1:99bfc8d68fd3 | 168 | |
| frankvnk | 1:99bfc8d68fd3 | 169 | |
| frankvnk | 1:99bfc8d68fd3 | 170 | int32_t cc3000_wlan::ioctl_del_profile(uint32_t index) { |
| frankvnk | 1:99bfc8d68fd3 | 171 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 172 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 173 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 174 | |
| frankvnk | 1:99bfc8d68fd3 | 175 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 176 | args = (uint8_t *)(ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 177 | |
| frankvnk | 1:99bfc8d68fd3 | 178 | // Fill in HCI packet structure |
| frankvnk | 1:99bfc8d68fd3 | 179 | args = UINT32_TO_STREAM(args, index); |
| frankvnk | 1:99bfc8d68fd3 | 180 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 181 | |
| frankvnk | 1:99bfc8d68fd3 | 182 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 183 | _hci.command_send(HCI_CMND_WLAN_IOCTL_DEL_PROFILE, ptr, WLAN_DEL_PROFILE_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 184 | |
| frankvnk | 1:99bfc8d68fd3 | 185 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 186 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_DEL_PROFILE, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 187 | |
| frankvnk | 1:99bfc8d68fd3 | 188 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 189 | } |
| frankvnk | 1:99bfc8d68fd3 | 190 | |
| frankvnk | 1:99bfc8d68fd3 | 191 | int32_t cc3000_wlan::set_event_mask(uint32_t mask) { |
| frankvnk | 1:99bfc8d68fd3 | 192 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 193 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 194 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 195 | |
| frankvnk | 1:99bfc8d68fd3 | 196 | |
| frankvnk | 1:99bfc8d68fd3 | 197 | if ((mask & HCI_EVNT_WLAN_TX_COMPLETE) == HCI_EVNT_WLAN_TX_COMPLETE) |
| frankvnk | 1:99bfc8d68fd3 | 198 | { |
| frankvnk | 1:99bfc8d68fd3 | 199 | _simple_link.set_tx_complete_signal(0); |
| frankvnk | 1:99bfc8d68fd3 | 200 | |
| frankvnk | 1:99bfc8d68fd3 | 201 | // Since an event is a virtual event - i.e. it is not coming from CC3000 |
| frankvnk | 1:99bfc8d68fd3 | 202 | // there is no need to send anything to the device if it was an only event |
| frankvnk | 1:99bfc8d68fd3 | 203 | if (mask == HCI_EVNT_WLAN_TX_COMPLETE) |
| frankvnk | 1:99bfc8d68fd3 | 204 | { |
| frankvnk | 1:99bfc8d68fd3 | 205 | return 0; |
| frankvnk | 1:99bfc8d68fd3 | 206 | } |
| frankvnk | 1:99bfc8d68fd3 | 207 | |
| frankvnk | 1:99bfc8d68fd3 | 208 | mask &= ~HCI_EVNT_WLAN_TX_COMPLETE; |
| frankvnk | 1:99bfc8d68fd3 | 209 | mask |= HCI_EVNT_WLAN_UNSOL_BASE; |
| frankvnk | 1:99bfc8d68fd3 | 210 | } |
| frankvnk | 1:99bfc8d68fd3 | 211 | else |
| frankvnk | 1:99bfc8d68fd3 | 212 | { |
| frankvnk | 1:99bfc8d68fd3 | 213 | _simple_link.set_tx_complete_signal(1); |
| frankvnk | 1:99bfc8d68fd3 | 214 | } |
| frankvnk | 1:99bfc8d68fd3 | 215 | |
| frankvnk | 1:99bfc8d68fd3 | 216 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 217 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 218 | args = (uint8_t *)(ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 219 | |
| frankvnk | 1:99bfc8d68fd3 | 220 | // Fill in HCI packet structure |
| frankvnk | 1:99bfc8d68fd3 | 221 | args = UINT32_TO_STREAM(args, mask); |
| frankvnk | 1:99bfc8d68fd3 | 222 | |
| frankvnk | 1:99bfc8d68fd3 | 223 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 224 | _hci.command_send(HCI_CMND_EVENT_MASK, ptr, WLAN_SET_MASK_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 225 | |
| frankvnk | 1:99bfc8d68fd3 | 226 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 227 | _event.simplelink_wait_event(HCI_CMND_EVENT_MASK, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 228 | |
| frankvnk | 1:99bfc8d68fd3 | 229 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 230 | } |
| frankvnk | 1:99bfc8d68fd3 | 231 | |
| frankvnk | 1:99bfc8d68fd3 | 232 | |
| frankvnk | 1:99bfc8d68fd3 | 233 | int32_t cc3000_wlan::smart_config_start(uint32_t encrypted_flag) { |
| frankvnk | 1:99bfc8d68fd3 | 234 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 235 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 236 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 237 | |
| frankvnk | 1:99bfc8d68fd3 | 238 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 239 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 240 | args = (uint8_t *)(ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 241 | |
| frankvnk | 1:99bfc8d68fd3 | 242 | // Fill in HCI packet structure |
| frankvnk | 1:99bfc8d68fd3 | 243 | args = UINT32_TO_STREAM(args, encrypted_flag); |
| frankvnk | 1:99bfc8d68fd3 | 244 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 245 | |
| frankvnk | 1:99bfc8d68fd3 | 246 | _hci.command_send(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_START, ptr, WLAN_SMART_CONFIG_START_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 247 | |
| frankvnk | 1:99bfc8d68fd3 | 248 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 249 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_START, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 250 | |
| frankvnk | 1:99bfc8d68fd3 | 251 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 252 | } |
| frankvnk | 1:99bfc8d68fd3 | 253 | |
| frankvnk | 1:99bfc8d68fd3 | 254 | |
| frankvnk | 1:99bfc8d68fd3 | 255 | int32_t cc3000_wlan::smart_config_stop(void) { |
| frankvnk | 1:99bfc8d68fd3 | 256 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 257 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 258 | |
| frankvnk | 1:99bfc8d68fd3 | 259 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 260 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 261 | |
| frankvnk | 1:99bfc8d68fd3 | 262 | _hci.command_send(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_STOP, ptr, 0); |
| frankvnk | 1:99bfc8d68fd3 | 263 | |
| frankvnk | 1:99bfc8d68fd3 | 264 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 265 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_STOP, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 266 | |
| frankvnk | 1:99bfc8d68fd3 | 267 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 268 | } |
| frankvnk | 1:99bfc8d68fd3 | 269 | |
| frankvnk | 1:99bfc8d68fd3 | 270 | int32_t cc3000_wlan::smart_config_set_prefix(uint8_t *new_prefix) { |
| frankvnk | 1:99bfc8d68fd3 | 271 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 272 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 273 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 274 | |
| frankvnk | 1:99bfc8d68fd3 | 275 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 276 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 277 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 278 | |
| frankvnk | 1:99bfc8d68fd3 | 279 | if (new_prefix == NULL) |
| frankvnk | 1:99bfc8d68fd3 | 280 | return ret; |
| frankvnk | 1:99bfc8d68fd3 | 281 | else // with the new Smart Config, prefix must be TTT |
| frankvnk | 1:99bfc8d68fd3 | 282 | { |
| frankvnk | 1:99bfc8d68fd3 | 283 | *new_prefix = 'T'; |
| frankvnk | 1:99bfc8d68fd3 | 284 | *(new_prefix + 1) = 'T'; |
| frankvnk | 1:99bfc8d68fd3 | 285 | *(new_prefix + 2) = 'T'; |
| frankvnk | 1:99bfc8d68fd3 | 286 | } |
| frankvnk | 1:99bfc8d68fd3 | 287 | |
| frankvnk | 1:99bfc8d68fd3 | 288 | ARRAY_TO_STREAM(args, new_prefix, SL_SIMPLE_CONFIG_PREFIX_LENGTH); |
| frankvnk | 1:99bfc8d68fd3 | 289 | |
| frankvnk | 1:99bfc8d68fd3 | 290 | _hci.command_send(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_SET_PREFIX, ptr, SL_SIMPLE_CONFIG_PREFIX_LENGTH); |
| frankvnk | 1:99bfc8d68fd3 | 291 | |
| frankvnk | 1:99bfc8d68fd3 | 292 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 293 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_SIMPLE_CONFIG_SET_PREFIX, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 294 | |
| frankvnk | 1:99bfc8d68fd3 | 295 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 296 | } |
| frankvnk | 1:99bfc8d68fd3 | 297 | |
| frankvnk | 1:99bfc8d68fd3 | 298 | #ifndef CC3000_TINY_DRIVER |
| frankvnk | 1:99bfc8d68fd3 | 299 | int32_t cc3000_wlan::connect(uint32_t sec_type, const uint8_t *ssid, int32_t ssid_len, uint8_t *bssid, |
| frankvnk | 1:99bfc8d68fd3 | 300 | uint8_t *key, int32_t key_len) { |
| frankvnk | 1:99bfc8d68fd3 | 301 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 302 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 303 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 304 | uint8_t bssid_zero[] = {0, 0, 0, 0, 0, 0}; |
| frankvnk | 1:99bfc8d68fd3 | 305 | |
| frankvnk | 1:99bfc8d68fd3 | 306 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 307 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 308 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 309 | |
| frankvnk | 1:99bfc8d68fd3 | 310 | // Fill in command buffer |
| frankvnk | 1:99bfc8d68fd3 | 311 | args = UINT32_TO_STREAM(args, 0x0000001c); |
| frankvnk | 1:99bfc8d68fd3 | 312 | args = UINT32_TO_STREAM(args, ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 313 | args = UINT32_TO_STREAM(args, sec_type); |
| frankvnk | 1:99bfc8d68fd3 | 314 | args = UINT32_TO_STREAM(args, 0x00000010 + ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 315 | args = UINT32_TO_STREAM(args, key_len); |
| frankvnk | 1:99bfc8d68fd3 | 316 | args = UINT16_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 317 | |
| frankvnk | 1:99bfc8d68fd3 | 318 | // padding shall be zeroed |
| frankvnk | 1:99bfc8d68fd3 | 319 | if(bssid) |
| frankvnk | 1:99bfc8d68fd3 | 320 | { |
| frankvnk | 1:99bfc8d68fd3 | 321 | ARRAY_TO_STREAM(args, bssid, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 322 | } |
| frankvnk | 1:99bfc8d68fd3 | 323 | else |
| frankvnk | 1:99bfc8d68fd3 | 324 | { |
| frankvnk | 1:99bfc8d68fd3 | 325 | ARRAY_TO_STREAM(args, bssid_zero, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 326 | } |
| frankvnk | 1:99bfc8d68fd3 | 327 | |
| frankvnk | 1:99bfc8d68fd3 | 328 | ARRAY_TO_STREAM(args, ssid, ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 329 | |
| frankvnk | 1:99bfc8d68fd3 | 330 | if(key_len && key) |
| frankvnk | 1:99bfc8d68fd3 | 331 | { |
| frankvnk | 1:99bfc8d68fd3 | 332 | ARRAY_TO_STREAM(args, key, key_len); |
| frankvnk | 1:99bfc8d68fd3 | 333 | } |
| frankvnk | 1:99bfc8d68fd3 | 334 | |
| frankvnk | 1:99bfc8d68fd3 | 335 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 336 | _hci.command_send(HCI_CMND_WLAN_CONNECT, ptr, WLAN_CONNECT_PARAM_LEN + ssid_len + key_len - 1); |
| frankvnk | 1:99bfc8d68fd3 | 337 | |
| frankvnk | 1:99bfc8d68fd3 | 338 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 339 | _event.simplelink_wait_event(HCI_CMND_WLAN_CONNECT, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 340 | errno = ret; |
| frankvnk | 1:99bfc8d68fd3 | 341 | |
| frankvnk | 1:99bfc8d68fd3 | 342 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 343 | } |
| frankvnk | 1:99bfc8d68fd3 | 344 | |
| frankvnk | 1:99bfc8d68fd3 | 345 | int32_t cc3000_wlan::add_profile(uint32_t sec_type, |
| frankvnk | 1:99bfc8d68fd3 | 346 | uint8_t* ssid, |
| frankvnk | 1:99bfc8d68fd3 | 347 | uint32_t ssid_length, |
| frankvnk | 1:99bfc8d68fd3 | 348 | uint8_t *b_ssid, |
| frankvnk | 1:99bfc8d68fd3 | 349 | uint32_t priority, |
| frankvnk | 1:99bfc8d68fd3 | 350 | uint32_t pairwise_cipher_or_tx_key_len, |
| frankvnk | 1:99bfc8d68fd3 | 351 | uint32_t group_cipher_tx_key_index, |
| frankvnk | 1:99bfc8d68fd3 | 352 | uint32_t key_mgmt, |
| frankvnk | 1:99bfc8d68fd3 | 353 | uint8_t* pf_or_key, |
| frankvnk | 1:99bfc8d68fd3 | 354 | uint32_t pass_phrase_len) { |
| frankvnk | 1:99bfc8d68fd3 | 355 | uint16_t arg_len = 0x00; |
| frankvnk | 1:99bfc8d68fd3 | 356 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 357 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 358 | int32_t i = 0; |
| frankvnk | 1:99bfc8d68fd3 | 359 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 360 | uint8_t bssid_zero[] = {0, 0, 0, 0, 0, 0}; |
| frankvnk | 1:99bfc8d68fd3 | 361 | |
| frankvnk | 1:99bfc8d68fd3 | 362 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 363 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 364 | |
| frankvnk | 1:99bfc8d68fd3 | 365 | args = UINT32_TO_STREAM(args, sec_type); |
| frankvnk | 1:99bfc8d68fd3 | 366 | |
| frankvnk | 1:99bfc8d68fd3 | 367 | // Setup arguments in accordance with the security type |
| frankvnk | 1:99bfc8d68fd3 | 368 | switch (sec_type) |
| frankvnk | 1:99bfc8d68fd3 | 369 | { |
| frankvnk | 1:99bfc8d68fd3 | 370 | //OPEN |
| frankvnk | 1:99bfc8d68fd3 | 371 | case WLAN_SEC_UNSEC: |
| frankvnk | 1:99bfc8d68fd3 | 372 | { |
| frankvnk | 1:99bfc8d68fd3 | 373 | args = UINT32_TO_STREAM(args, 0x00000014); |
| frankvnk | 1:99bfc8d68fd3 | 374 | args = UINT32_TO_STREAM(args, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 375 | args = UINT16_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 376 | if(b_ssid) |
| frankvnk | 1:99bfc8d68fd3 | 377 | { |
| frankvnk | 1:99bfc8d68fd3 | 378 | ARRAY_TO_STREAM(args, b_ssid, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 379 | } |
| frankvnk | 1:99bfc8d68fd3 | 380 | else |
| frankvnk | 1:99bfc8d68fd3 | 381 | { |
| frankvnk | 1:99bfc8d68fd3 | 382 | ARRAY_TO_STREAM(args, bssid_zero, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 383 | } |
| frankvnk | 1:99bfc8d68fd3 | 384 | args = UINT32_TO_STREAM(args, priority); |
| frankvnk | 1:99bfc8d68fd3 | 385 | ARRAY_TO_STREAM(args, ssid, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 386 | |
| frankvnk | 1:99bfc8d68fd3 | 387 | arg_len = WLAN_ADD_PROFILE_NOSEC_PARAM_LEN + ssid_length; |
| frankvnk | 1:99bfc8d68fd3 | 388 | } |
| frankvnk | 1:99bfc8d68fd3 | 389 | break; |
| frankvnk | 1:99bfc8d68fd3 | 390 | |
| frankvnk | 1:99bfc8d68fd3 | 391 | //WEP |
| frankvnk | 1:99bfc8d68fd3 | 392 | case WLAN_SEC_WEP: |
| frankvnk | 1:99bfc8d68fd3 | 393 | { |
| frankvnk | 1:99bfc8d68fd3 | 394 | args = UINT32_TO_STREAM(args, 0x00000020); |
| frankvnk | 1:99bfc8d68fd3 | 395 | args = UINT32_TO_STREAM(args, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 396 | args = UINT16_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 397 | if(b_ssid) |
| frankvnk | 1:99bfc8d68fd3 | 398 | { |
| frankvnk | 1:99bfc8d68fd3 | 399 | ARRAY_TO_STREAM(args, b_ssid, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 400 | } |
| frankvnk | 1:99bfc8d68fd3 | 401 | else |
| frankvnk | 1:99bfc8d68fd3 | 402 | { |
| frankvnk | 1:99bfc8d68fd3 | 403 | ARRAY_TO_STREAM(args, bssid_zero, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 404 | } |
| frankvnk | 1:99bfc8d68fd3 | 405 | args = UINT32_TO_STREAM(args, priority); |
| frankvnk | 1:99bfc8d68fd3 | 406 | args = UINT32_TO_STREAM(args, 0x0000000C + ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 407 | args = UINT32_TO_STREAM(args, pairwise_cipher_or_tx_key_len); |
| frankvnk | 1:99bfc8d68fd3 | 408 | args = UINT32_TO_STREAM(args, group_cipher_tx_key_index); |
| frankvnk | 1:99bfc8d68fd3 | 409 | ARRAY_TO_STREAM(args, ssid, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 410 | |
| frankvnk | 1:99bfc8d68fd3 | 411 | for(i = 0; i < 4; i++) |
| frankvnk | 1:99bfc8d68fd3 | 412 | { |
| frankvnk | 1:99bfc8d68fd3 | 413 | uint8_t *p = &pf_or_key[i * pairwise_cipher_or_tx_key_len]; |
| frankvnk | 1:99bfc8d68fd3 | 414 | |
| frankvnk | 1:99bfc8d68fd3 | 415 | ARRAY_TO_STREAM(args, p, pairwise_cipher_or_tx_key_len); |
| frankvnk | 1:99bfc8d68fd3 | 416 | } |
| frankvnk | 1:99bfc8d68fd3 | 417 | |
| frankvnk | 1:99bfc8d68fd3 | 418 | arg_len = WLAN_ADD_PROFILE_WEP_PARAM_LEN + ssid_length + |
| frankvnk | 1:99bfc8d68fd3 | 419 | pairwise_cipher_or_tx_key_len * 4; |
| frankvnk | 1:99bfc8d68fd3 | 420 | |
| frankvnk | 1:99bfc8d68fd3 | 421 | } |
| frankvnk | 1:99bfc8d68fd3 | 422 | break; |
| frankvnk | 1:99bfc8d68fd3 | 423 | |
| frankvnk | 1:99bfc8d68fd3 | 424 | //WPA |
| frankvnk | 1:99bfc8d68fd3 | 425 | //WPA2 |
| frankvnk | 1:99bfc8d68fd3 | 426 | case WLAN_SEC_WPA: |
| frankvnk | 1:99bfc8d68fd3 | 427 | case WLAN_SEC_WPA2: |
| frankvnk | 1:99bfc8d68fd3 | 428 | { |
| frankvnk | 1:99bfc8d68fd3 | 429 | args = UINT32_TO_STREAM(args, 0x00000028); |
| frankvnk | 1:99bfc8d68fd3 | 430 | args = UINT32_TO_STREAM(args, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 431 | args = UINT16_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 432 | if(b_ssid) |
| frankvnk | 1:99bfc8d68fd3 | 433 | { |
| frankvnk | 1:99bfc8d68fd3 | 434 | ARRAY_TO_STREAM(args, b_ssid, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 435 | } |
| frankvnk | 1:99bfc8d68fd3 | 436 | else |
| frankvnk | 1:99bfc8d68fd3 | 437 | { |
| frankvnk | 1:99bfc8d68fd3 | 438 | ARRAY_TO_STREAM(args, bssid_zero, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 439 | } |
| frankvnk | 1:99bfc8d68fd3 | 440 | args = UINT32_TO_STREAM(args, priority); |
| frankvnk | 1:99bfc8d68fd3 | 441 | args = UINT32_TO_STREAM(args, pairwise_cipher_or_tx_key_len); |
| frankvnk | 1:99bfc8d68fd3 | 442 | args = UINT32_TO_STREAM(args, group_cipher_tx_key_index); |
| frankvnk | 1:99bfc8d68fd3 | 443 | args = UINT32_TO_STREAM(args, key_mgmt); |
| frankvnk | 1:99bfc8d68fd3 | 444 | args = UINT32_TO_STREAM(args, 0x00000008 + ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 445 | args = UINT32_TO_STREAM(args, pass_phrase_len); |
| frankvnk | 1:99bfc8d68fd3 | 446 | ARRAY_TO_STREAM(args, ssid, ssid_length); |
| frankvnk | 1:99bfc8d68fd3 | 447 | ARRAY_TO_STREAM(args, pf_or_key, pass_phrase_len); |
| frankvnk | 1:99bfc8d68fd3 | 448 | |
| frankvnk | 1:99bfc8d68fd3 | 449 | arg_len = WLAN_ADD_PROFILE_WPA_PARAM_LEN + ssid_length + pass_phrase_len; |
| frankvnk | 1:99bfc8d68fd3 | 450 | } |
| frankvnk | 1:99bfc8d68fd3 | 451 | |
| frankvnk | 1:99bfc8d68fd3 | 452 | break; |
| frankvnk | 1:99bfc8d68fd3 | 453 | } |
| frankvnk | 1:99bfc8d68fd3 | 454 | |
| frankvnk | 1:99bfc8d68fd3 | 455 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 456 | _hci.command_send(HCI_CMND_WLAN_IOCTL_ADD_PROFILE, ptr, arg_len); |
| frankvnk | 1:99bfc8d68fd3 | 457 | |
| frankvnk | 1:99bfc8d68fd3 | 458 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 459 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_ADD_PROFILE, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 460 | |
| frankvnk | 1:99bfc8d68fd3 | 461 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 462 | } |
| frankvnk | 1:99bfc8d68fd3 | 463 | |
| frankvnk | 1:99bfc8d68fd3 | 464 | int32_t cc3000_wlan::ioctl_get_scan_results(uint32_t scan_timeout, uint8_t *results) { |
| frankvnk | 1:99bfc8d68fd3 | 465 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 466 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 467 | |
| frankvnk | 1:99bfc8d68fd3 | 468 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 469 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 470 | |
| frankvnk | 1:99bfc8d68fd3 | 471 | // Fill in temporary command buffer |
| frankvnk | 1:99bfc8d68fd3 | 472 | args = UINT32_TO_STREAM(args, scan_timeout); |
| frankvnk | 1:99bfc8d68fd3 | 473 | |
| frankvnk | 1:99bfc8d68fd3 | 474 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 475 | _hci.command_send(HCI_CMND_WLAN_IOCTL_GET_SCAN_RESULTS, ptr, WLAN_GET_SCAN_RESULTS_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 476 | |
| frankvnk | 1:99bfc8d68fd3 | 477 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 478 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_GET_SCAN_RESULTS, results); |
| frankvnk | 1:99bfc8d68fd3 | 479 | |
| frankvnk | 1:99bfc8d68fd3 | 480 | return(0); |
| frankvnk | 1:99bfc8d68fd3 | 481 | } |
| frankvnk | 1:99bfc8d68fd3 | 482 | |
| frankvnk | 1:99bfc8d68fd3 | 483 | int32_t cc3000_wlan::ioctl_set_scan_params(uint32_t enable, |
| frankvnk | 1:99bfc8d68fd3 | 484 | uint32_t min_dwell_time, |
| frankvnk | 1:99bfc8d68fd3 | 485 | uint32_t max_dwell_time, |
| frankvnk | 1:99bfc8d68fd3 | 486 | uint32_t num_probe_requests, |
| frankvnk | 1:99bfc8d68fd3 | 487 | uint32_t channel_mask, |
| frankvnk | 1:99bfc8d68fd3 | 488 | int32_t rssi_threshold, |
| frankvnk | 1:99bfc8d68fd3 | 489 | uint32_t snr_threshold, |
| frankvnk | 1:99bfc8d68fd3 | 490 | uint32_t default_tx_power, |
| frankvnk | 1:99bfc8d68fd3 | 491 | uint32_t *interval_list) { |
| frankvnk | 1:99bfc8d68fd3 | 492 | uint32_t uiRes; |
| frankvnk | 1:99bfc8d68fd3 | 493 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 494 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 495 | |
| frankvnk | 1:99bfc8d68fd3 | 496 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 497 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 498 | |
| frankvnk | 1:99bfc8d68fd3 | 499 | // Fill in temporary command buffer |
| frankvnk | 1:99bfc8d68fd3 | 500 | args = UINT32_TO_STREAM(args, 36); |
| frankvnk | 1:99bfc8d68fd3 | 501 | args = UINT32_TO_STREAM(args, enable); |
| frankvnk | 1:99bfc8d68fd3 | 502 | args = UINT32_TO_STREAM(args, min_dwell_time); |
| frankvnk | 1:99bfc8d68fd3 | 503 | args = UINT32_TO_STREAM(args, max_dwell_time); |
| frankvnk | 1:99bfc8d68fd3 | 504 | args = UINT32_TO_STREAM(args, num_probe_requests); |
| frankvnk | 1:99bfc8d68fd3 | 505 | args = UINT32_TO_STREAM(args, channel_mask); |
| frankvnk | 1:99bfc8d68fd3 | 506 | args = UINT32_TO_STREAM(args, rssi_threshold); |
| frankvnk | 1:99bfc8d68fd3 | 507 | args = UINT32_TO_STREAM(args, snr_threshold); |
| frankvnk | 1:99bfc8d68fd3 | 508 | args = UINT32_TO_STREAM(args, default_tx_power); |
| frankvnk | 1:99bfc8d68fd3 | 509 | ARRAY_TO_STREAM(args, interval_list, sizeof(uint32_t) * SL_SET_SCAN_PARAMS_INTERVAL_LIST_SIZE); |
| frankvnk | 1:99bfc8d68fd3 | 510 | |
| frankvnk | 1:99bfc8d68fd3 | 511 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 512 | _hci.command_send(HCI_CMND_WLAN_IOCTL_SET_SCANPARAM, ptr, WLAN_SET_SCAN_PARAMS_LEN); |
| frankvnk | 1:99bfc8d68fd3 | 513 | |
| frankvnk | 1:99bfc8d68fd3 | 514 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 515 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_SET_SCANPARAM, &uiRes); |
| frankvnk | 1:99bfc8d68fd3 | 516 | |
| frankvnk | 1:99bfc8d68fd3 | 517 | return(uiRes); |
| frankvnk | 1:99bfc8d68fd3 | 518 | } |
| frankvnk | 1:99bfc8d68fd3 | 519 | |
| frankvnk | 1:99bfc8d68fd3 | 520 | int32_t cc3000_wlan::ioctl_statusget(void) { |
| frankvnk | 1:99bfc8d68fd3 | 521 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 522 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 523 | |
| frankvnk | 1:99bfc8d68fd3 | 524 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 525 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 526 | |
| frankvnk | 1:99bfc8d68fd3 | 527 | _hci.command_send(HCI_CMND_WLAN_IOCTL_STATUSGET,ptr, 0); |
| frankvnk | 1:99bfc8d68fd3 | 528 | |
| frankvnk | 1:99bfc8d68fd3 | 529 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 530 | _event.simplelink_wait_event(HCI_CMND_WLAN_IOCTL_STATUSGET, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 531 | |
| frankvnk | 1:99bfc8d68fd3 | 532 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 533 | } |
| frankvnk | 1:99bfc8d68fd3 | 534 | |
| frankvnk | 1:99bfc8d68fd3 | 535 | #else |
| frankvnk | 1:99bfc8d68fd3 | 536 | int32_t cc3000_wlan::wlan_add_profile(uint32_t sec_type, |
| frankvnk | 1:99bfc8d68fd3 | 537 | uint8_t *ssid, |
| frankvnk | 1:99bfc8d68fd3 | 538 | uint32_t ssid_length, |
| frankvnk | 1:99bfc8d68fd3 | 539 | uint8_t *b_ssid, |
| frankvnk | 1:99bfc8d68fd3 | 540 | uint32_t priority, |
| frankvnk | 1:99bfc8d68fd3 | 541 | uint32_t pairwise_cipher_or_tx_key_len, |
| frankvnk | 1:99bfc8d68fd3 | 542 | uint32_t group_cipher_tx_key_index, |
| frankvnk | 1:99bfc8d68fd3 | 543 | uint32_t key_mgmt, |
| frankvnk | 1:99bfc8d68fd3 | 544 | uint8_t* pf_or_key, |
| frankvnk | 1:99bfc8d68fd3 | 545 | uint32_t pass_phrase_length) |
| frankvnk | 1:99bfc8d68fd3 | 546 | { |
| frankvnk | 1:99bfc8d68fd3 | 547 | return -1; |
| frankvnk | 1:99bfc8d68fd3 | 548 | } |
| frankvnk | 1:99bfc8d68fd3 | 549 | |
| frankvnk | 1:99bfc8d68fd3 | 550 | int32_t cc3000_wlan::connect(const uint8_t *ssid, int32_t ssid_len) { |
| frankvnk | 1:99bfc8d68fd3 | 551 | int32_t ret; |
| frankvnk | 1:99bfc8d68fd3 | 552 | uint8_t *ptr; |
| frankvnk | 1:99bfc8d68fd3 | 553 | uint8_t *args; |
| frankvnk | 1:99bfc8d68fd3 | 554 | uint8_t bssid_zero[] = {0, 0, 0, 0, 0, 0}; |
| frankvnk | 1:99bfc8d68fd3 | 555 | |
| frankvnk | 1:99bfc8d68fd3 | 556 | ret = EFAIL; |
| frankvnk | 1:99bfc8d68fd3 | 557 | ptr = _simple_link.get_transmit_buffer(); |
| frankvnk | 1:99bfc8d68fd3 | 558 | args = (ptr + HEADERS_SIZE_CMD); |
| frankvnk | 1:99bfc8d68fd3 | 559 | |
| frankvnk | 1:99bfc8d68fd3 | 560 | // Fill in command buffer |
| frankvnk | 1:99bfc8d68fd3 | 561 | args = UINT32_TO_STREAM(args, 0x0000001c); |
| frankvnk | 1:99bfc8d68fd3 | 562 | args = UINT32_TO_STREAM(args, ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 563 | args = UINT32_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 564 | args = UINT32_TO_STREAM(args, 0x00000010 + ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 565 | args = UINT32_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 566 | args = UINT16_TO_STREAM(args, 0); |
| frankvnk | 1:99bfc8d68fd3 | 567 | |
| frankvnk | 1:99bfc8d68fd3 | 568 | // padding shall be zeroed |
| frankvnk | 1:99bfc8d68fd3 | 569 | ARRAY_TO_STREAM(args, bssid_zero, ETH_ALEN); |
| frankvnk | 1:99bfc8d68fd3 | 570 | ARRAY_TO_STREAM(args, ssid, ssid_len); |
| frankvnk | 1:99bfc8d68fd3 | 571 | |
| frankvnk | 1:99bfc8d68fd3 | 572 | // Initiate a HCI command |
| frankvnk | 1:99bfc8d68fd3 | 573 | _hci.command_send(HCI_CMND_WLAN_CONNECT, ptr, WLAN_CONNECT_PARAM_LEN + ssid_len - 1); |
| frankvnk | 1:99bfc8d68fd3 | 574 | |
| frankvnk | 1:99bfc8d68fd3 | 575 | // Wait for command complete event |
| frankvnk | 1:99bfc8d68fd3 | 576 | _event.simplelink_wait_event(HCI_CMND_WLAN_CONNECT, &ret); |
| frankvnk | 1:99bfc8d68fd3 | 577 | errno = ret; |
| frankvnk | 1:99bfc8d68fd3 | 578 | |
| frankvnk | 1:99bfc8d68fd3 | 579 | return(ret); |
| frankvnk | 1:99bfc8d68fd3 | 580 | } |
| frankvnk | 1:99bfc8d68fd3 | 581 | #endif |
| frankvnk | 1:99bfc8d68fd3 | 582 | |
| frankvnk | 1:99bfc8d68fd3 | 583 | |
| frankvnk | 1:99bfc8d68fd3 | 584 | |
| frankvnk | 1:99bfc8d68fd3 | 585 | #ifndef CC3000_UNENCRYPTED_SMART_CONFIG |
| frankvnk | 1:99bfc8d68fd3 | 586 | int32_t cc3000_wlan::smart_config_process(void) { |
| frankvnk | 1:99bfc8d68fd3 | 587 | int32_t returnValue; |
| frankvnk | 1:99bfc8d68fd3 | 588 | uint32_t ssidLen, keyLen; |
| frankvnk | 1:99bfc8d68fd3 | 589 | uint8_t *decKeyPtr; |
| frankvnk | 1:99bfc8d68fd3 | 590 | uint8_t *ssidPtr; |
| frankvnk | 1:99bfc8d68fd3 | 591 | |
| frankvnk | 1:99bfc8d68fd3 | 592 | // read the key from EEPROM - fileID 12 |
| frankvnk | 1:99bfc8d68fd3 | 593 | returnValue = aes_read_key(key); |
| frankvnk | 1:99bfc8d68fd3 | 594 | |
| frankvnk | 1:99bfc8d68fd3 | 595 | if (returnValue != 0) |
| frankvnk | 1:99bfc8d68fd3 | 596 | return returnValue; |
| frankvnk | 1:99bfc8d68fd3 | 597 | |
| frankvnk | 1:99bfc8d68fd3 | 598 | // read the received data from fileID #13 and parse it according to the followings: |
| frankvnk | 1:99bfc8d68fd3 | 599 | // 1) SSID LEN - not encrypted |
| frankvnk | 1:99bfc8d68fd3 | 600 | // 2) SSID - not encrypted |
| frankvnk | 1:99bfc8d68fd3 | 601 | // 3) KEY LEN - not encrypted. always 32 bytes long |
| frankvnk | 1:99bfc8d68fd3 | 602 | // 4) Security type - not encrypted |
| frankvnk | 1:99bfc8d68fd3 | 603 | // 5) KEY - encrypted together with true key length as the first byte in KEY |
| frankvnk | 1:99bfc8d68fd3 | 604 | // to elaborate, there are two corner cases: |
| frankvnk | 1:99bfc8d68fd3 | 605 | // 1) the KEY is 32 bytes long. In this case, the first byte does not represent KEY length |
| frankvnk | 1:99bfc8d68fd3 | 606 | // 2) the KEY is 31 bytes long. In this case, the first byte represent KEY length and equals 31 |
| frankvnk | 1:99bfc8d68fd3 | 607 | returnValue = nvmem_read(NVMEM_SHARED_MEM_FILEID, SMART_CONFIG_PROFILE_SIZE, 0, profileArray); |
| frankvnk | 1:99bfc8d68fd3 | 608 | |
| frankvnk | 1:99bfc8d68fd3 | 609 | if (returnValue != 0) |
| frankvnk | 1:99bfc8d68fd3 | 610 | return returnValue; |
| frankvnk | 1:99bfc8d68fd3 | 611 | |
| frankvnk | 1:99bfc8d68fd3 | 612 | ssidPtr = &profileArray[1]; |
| frankvnk | 1:99bfc8d68fd3 | 613 | |
| frankvnk | 1:99bfc8d68fd3 | 614 | ssidLen = profileArray[0]; |
| frankvnk | 1:99bfc8d68fd3 | 615 | |
| frankvnk | 1:99bfc8d68fd3 | 616 | decKeyPtr = &profileArray[profileArray[0] + 3]; |
| frankvnk | 1:99bfc8d68fd3 | 617 | |
| frankvnk | 1:99bfc8d68fd3 | 618 | aes_decrypt(decKeyPtr, key); |
| frankvnk | 1:99bfc8d68fd3 | 619 | if (profileArray[profileArray[0] + 1] > 16) |
| frankvnk | 1:99bfc8d68fd3 | 620 | aes_decrypt((uint8_t *)(decKeyPtr + 16), key); |
| frankvnk | 1:99bfc8d68fd3 | 621 | |
| frankvnk | 1:99bfc8d68fd3 | 622 | if (*(uint8_t *)(decKeyPtr +31) != 0) |
| frankvnk | 1:99bfc8d68fd3 | 623 | { |
| frankvnk | 1:99bfc8d68fd3 | 624 | if (*decKeyPtr == 31) |
| frankvnk | 1:99bfc8d68fd3 | 625 | { |
| frankvnk | 1:99bfc8d68fd3 | 626 | keyLen = 31; |
| frankvnk | 1:99bfc8d68fd3 | 627 | decKeyPtr++; |
| frankvnk | 1:99bfc8d68fd3 | 628 | } |
| frankvnk | 1:99bfc8d68fd3 | 629 | else |
| frankvnk | 1:99bfc8d68fd3 | 630 | { |
| frankvnk | 1:99bfc8d68fd3 | 631 | keyLen = 32; |
| frankvnk | 1:99bfc8d68fd3 | 632 | } |
| frankvnk | 1:99bfc8d68fd3 | 633 | } |
| frankvnk | 1:99bfc8d68fd3 | 634 | else |
| frankvnk | 1:99bfc8d68fd3 | 635 | { |
| frankvnk | 1:99bfc8d68fd3 | 636 | keyLen = *decKeyPtr; |
| frankvnk | 1:99bfc8d68fd3 | 637 | decKeyPtr++; |
| frankvnk | 1:99bfc8d68fd3 | 638 | } |
| frankvnk | 1:99bfc8d68fd3 | 639 | |
| frankvnk | 1:99bfc8d68fd3 | 640 | // add a profile |
| frankvnk | 1:99bfc8d68fd3 | 641 | switch (profileArray[profileArray[0] + 2]) |
| frankvnk | 1:99bfc8d68fd3 | 642 | { |
| frankvnk | 1:99bfc8d68fd3 | 643 | case WLAN_SEC_UNSEC://None |
| frankvnk | 1:99bfc8d68fd3 | 644 | { |
| frankvnk | 1:99bfc8d68fd3 | 645 | returnValue = wlan_add_profile(profileArray[profileArray[0] + 2], // security type |
| frankvnk | 1:99bfc8d68fd3 | 646 | ssidPtr, // SSID |
| frankvnk | 1:99bfc8d68fd3 | 647 | ssidLen, // SSID length |
| frankvnk | 1:99bfc8d68fd3 | 648 | NULL, // BSSID |
| frankvnk | 1:99bfc8d68fd3 | 649 | 1, // Priority |
| frankvnk | 1:99bfc8d68fd3 | 650 | 0, 0, 0, 0, 0); |
| frankvnk | 1:99bfc8d68fd3 | 651 | |
| frankvnk | 1:99bfc8d68fd3 | 652 | break; |
| frankvnk | 1:99bfc8d68fd3 | 653 | } |
| frankvnk | 1:99bfc8d68fd3 | 654 | |
| frankvnk | 1:99bfc8d68fd3 | 655 | case WLAN_SEC_WEP://WEP |
| frankvnk | 1:99bfc8d68fd3 | 656 | { |
| frankvnk | 1:99bfc8d68fd3 | 657 | returnValue = wlan_add_profile(profileArray[profileArray[0] + 2], // security type |
| frankvnk | 1:99bfc8d68fd3 | 658 | ssidPtr, // SSID |
| frankvnk | 1:99bfc8d68fd3 | 659 | ssidLen, // SSID length |
| frankvnk | 1:99bfc8d68fd3 | 660 | NULL, // BSSID |
| frankvnk | 1:99bfc8d68fd3 | 661 | 1, // Priority |
| frankvnk | 1:99bfc8d68fd3 | 662 | keyLen, // KEY length |
| frankvnk | 1:99bfc8d68fd3 | 663 | 0, // KEY index |
| frankvnk | 1:99bfc8d68fd3 | 664 | 0, |
| frankvnk | 1:99bfc8d68fd3 | 665 | decKeyPtr, // KEY |
| frankvnk | 1:99bfc8d68fd3 | 666 | 0); |
| frankvnk | 1:99bfc8d68fd3 | 667 | |
| frankvnk | 1:99bfc8d68fd3 | 668 | break; |
| frankvnk | 1:99bfc8d68fd3 | 669 | } |
| frankvnk | 1:99bfc8d68fd3 | 670 | |
| frankvnk | 1:99bfc8d68fd3 | 671 | case WLAN_SEC_WPA: //WPA |
| frankvnk | 1:99bfc8d68fd3 | 672 | case WLAN_SEC_WPA2: //WPA2 |
| frankvnk | 1:99bfc8d68fd3 | 673 | { |
| frankvnk | 1:99bfc8d68fd3 | 674 | returnValue = wlan_add_profile(WLAN_SEC_WPA2, // security type |
| frankvnk | 1:99bfc8d68fd3 | 675 | ssidPtr, |
| frankvnk | 1:99bfc8d68fd3 | 676 | ssidLen, |
| frankvnk | 1:99bfc8d68fd3 | 677 | NULL, // BSSID |
| frankvnk | 1:99bfc8d68fd3 | 678 | 1, // Priority |
| frankvnk | 1:99bfc8d68fd3 | 679 | 0x18, // PairwiseCipher |
| frankvnk | 1:99bfc8d68fd3 | 680 | 0x1e, // GroupCipher |
| frankvnk | 1:99bfc8d68fd3 | 681 | 2, // KEY management |
| frankvnk | 1:99bfc8d68fd3 | 682 | decKeyPtr, // KEY |
| frankvnk | 1:99bfc8d68fd3 | 683 | keyLen); // KEY length |
| frankvnk | 1:99bfc8d68fd3 | 684 | |
| frankvnk | 1:99bfc8d68fd3 | 685 | break; |
| frankvnk | 1:99bfc8d68fd3 | 686 | } |
| frankvnk | 1:99bfc8d68fd3 | 687 | } |
| frankvnk | 1:99bfc8d68fd3 | 688 | |
| frankvnk | 1:99bfc8d68fd3 | 689 | return returnValue; |
| frankvnk | 1:99bfc8d68fd3 | 690 | } |
| frankvnk | 1:99bfc8d68fd3 | 691 | #endif |
| frankvnk | 1:99bfc8d68fd3 | 692 | |
| frankvnk | 1:99bfc8d68fd3 | 693 | } |
 Avnet Wi-Go System
Avnet Wi-Go System